Encryption is an amazing thing. Without it, all of our data would be flying about in cyberspace, in plain text, for anyone to read! Not only that… But, cryptocurrency wouldn’t exist.
Encryption is used on many levels, for example… Sending information to your router, or even for storing your password to your favorite website.
Encryption helps insure that in the event of a leak/violation of data… The data is unreadable(or, at least harder to read).
Who Created Encryption Standards?
In order for encryption to be adopted on a massive scale across the internet, a party of sorts had to create and advocate specific algorithms. This would help ensure that there wasn’t any major conflict between different types of encryption, and which use-case is acceptable for which algorithm.
That party happened to be the NSA(National Security Agency). Makes sense… I think.
(There are also encryption algorithms that were created without the NSA, however they are not nearly as popular… So, I’m skipping them.)
The NSA’s History
The NSA has done an amazing public service for all users of the internet, by creating the standards for encryption… From SHA-0, to AES-256! There’s tons of different and loved/widely used algorithms that exist only because of their participation…
The NSA’s most appealing algorithm to cryptocurrency enthusiasts is called SHA(Secure Hash Algorithm), but it might not have as nice of a track record as you’d like.
What’s The Issue?
The cryptographic algorithm that Bitcoin and many other blockchains utilize is called SHA-256, which is a SHA-2 variation that was indeed created by the NSA. Who’s to say the NSA doesn’t hold some special kind of key to crack anything encrypted in SHA-256? This is the issue in relying on a single party. The unknown.
At the end of the day, the only thing that crypto enthusiasts care about, is decentralization. If a decentralized cryptocurrency relies on an encryption algorithm created by a single party… Is it really decentralized?
I imagine you can see the possible issue here…
Could There Be A Magic Key?
Who knows? If it makes you feel better, there’s been no known magical crack of the algorithm to date… But, if you’re more concerned, get a load of this…
SHA-0, and SHA-1, have been figured out. They can all be decrypted efficiently, and quickly by initially only the NSA, then regular users after the technology had trickled downward.
MD5 is among the worst encryption algorithms that you can adopt in modern times… As it’s, “mostly” crackable. “Why does MD5 matter?” you ask? it’s closely related to the SHA algorithm, and is another step toward SHA-2.
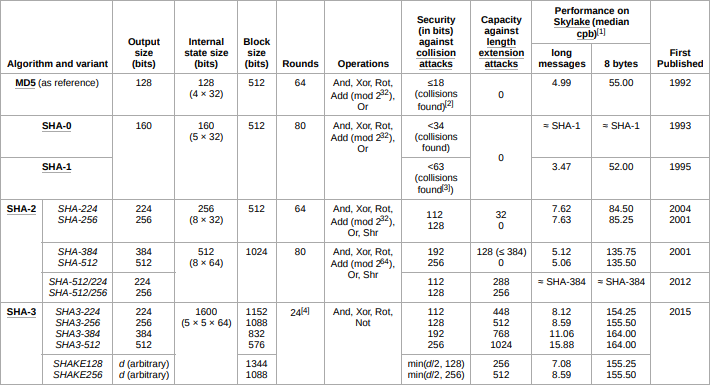
It’s only a matter of time, before the NSA become the first known organization to crack SHA-2. Although, that time is unforeseeable… It will for sure happen eventually, and by then there will likely be a new, and better algorithm. The question is not how, but when.
If Bitcoin and similar blockchain’s were to stick with SHA-2 long enough for NSA to figure out how to crack it, do you think that the NSA would attack cryptocurrencies using the algorithm? Or, would they sit, and do nothing?
Why Don’t Blockchains And Other Applications Use SHA-3?
It’s the newer, and inherently more complicated algorithm, no? Why isn’t it implemented in blockchain technology?
Well… SHA-3 is an incredibly new method for encryption, and is nothing like it’s SHA-2 predecessor. We don’t really now how to efficiently work with it yet. If you’re looking for more information as to how it works, check it out here.
Are You Safe Using SHA-256?
What are the odds that the NSA does hold a magical key, that hasn’t been exposed yet? Slim to none. If it hasn’t been cracked yet, you really have no reason to worry. Surely, by the time it is crackable(with the power of quantum computing), there will be bigger and better encryption algorithms leading the same unknown path into the future. Who knows, maybe SHA-3 will have been properly adopted by said time.
In Conclusion
In conclusion, the NSA created the standards that we have for encryption. This includes most of the standards used in cryptocurrency/blockchain technology. The fact that a single party, created the algorithm used for encryption in a sense centralizes it(but, not really).
If the NSA were to have some sort of secret key to crack SHA-2 I’m sure we’d know about it by now. Whenever SHA-2 is crackable, they’ll be the ones to crack it first… And time will come.
For now, we’re safe but who knows if we will be in ten years from now?




0 Comments